I just want to put this disclaimer out there first before I show an example of a Mobile Man in the Middle (MiTM) Attack. I do not accept any liability whatsoever for the content, or for the consequences of any action taken on the basis of the information provided. This is just a proof-of-concept example illustrating how a Mobile MiTM Attack would be carried out; therefore this information should only be used for educational purposes.
Here’s a classic scenario using an Android Mobile Device to act as a MiTM to eavesdrop on a User’s Internet activity.
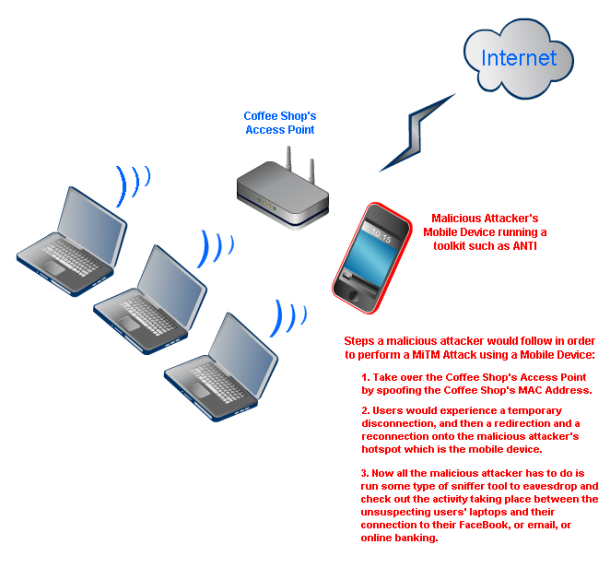
People generally go to coffee shops to grab a quick lunch, get some coffee, socialize, work, etc. People also tend to bring along their laptops because most coffees shops offer free WiFi. Almost all users have their WiFi settings to connect automatically to the nearest WiFi Access Point. Users don’t know any better and are not usually aware of whether they connected to a trusted WiFi or not. Users also do not know the implications of connecting to an untrusted WiFi Access Point. Once users are connected to the Internet they may access their Facebook page, email account, and online bank account. All is well as far as the user is concerned. General users are not aware of all the bad deeds a malicious attacker can peform at their local coffee shop.
Figure 1 – Illustration of a Mobile Based MiTM Attack
A malicious attacker would have a mobile device that has the ability to provide hotspot access; therefore they can act as an access point at the coffee shop and provide Internet access for all the users. So instead of a user connecting to the coffee shop’s Access Point they would be connected to the malicious attacker’s Access Point or Hotspot. Essentially, the malicious attacker has taken over the coffee shop’s Access Point and set his own into place so users would connect to his hotspot. At this point all users connecting to the malicious attacker’s hotspot would have their Internet connections going through the malicious attacker’s hotspot. Now all Internet activity conducted by the users can be viewed by the malicious attacker. This is a man in the middle attack. The malicious attacker was able to hijack all wireless connection requests from the users and had them connect to his/her hotspot. He/She is now able to eavesdrop without any issues on all connected users.
I wrote about a tool before that would allow you to do all of this. Check out my post on the Android Network Toolkit. Here’s a link for you: https://michaelkaishar.wordpress.com/2011/12/21/android-network-toolkit/
Regards,
Michael Kaishar, MSIA | CISSP
Disclaimer: This post is solely for educational purposes. The author does not accept any liability whatsoever for the content, or for the consequences of any action taken on the basis of the informatioin provided.